SECURANCE™
Atlanta’s Best Cyber Security Company
“Relying on security software alone to protect your systems and data is a dangerous strategy…”
Securance is a multi-layer managed security solution for small to medium-sized businesses in the Southeast. It’s the first line of defense in our philosophy of protection, detection, and mitigation. We identified as early as 2011 that relying solely on your security software to keep your information safe is a really dangerous strategy and lulls you into a false sense of security. As counter-intuitive as it may seem, as an information technology company in Atlanta GA, we have built our strategy on the assumption that security software will fail. We cannot totally prevent security breaches. There, we admit it.
Built on the NIST (National Institute of Standards and Technology) proven collection of best security products, Securance protocols were designed to provide multiple layers of protection against known threats. Because we assume each layer to only be moderately effective, we not only rely on the product but also use third-party tools to identify threats as they arise. Each component of Securance is linked to a different component that handles detection in the event that the primary system fails.
Ultimately, however, all levels of protection are subject to failure in the world of cybersecurity. CloudSurance is our backup in the very likely event that Securance fails.
Cybersecurity is not just a firewall, an anti-virus software, or an intrusion detection system. Those are all tools to be used in the pursuit of creating a cybersecurity system for your business. Cybersecurity companies in Atlanta have long touted that you need “X or Y” systems to be secure in their never-ending quest to sell more boxes and more subscriptions.
The simple fact though, is that a true cyber security company will realize that cyber security is a combination of tools, protocols, policies, and behaviors designed to fit into your workflows and systems in order to achieve a level of acceptable security. In short, Cyber Security is a business risk management exercise and not a 100% technical exercise.
Securance is just that, it is a combination of systems, services, and policies to achieve a level of cyber security that fits into your existing systems. Securance is a complete package representing the new standard in what you need to have and do. Not only does it contain all the bits and pieces required, but it also encompasses the necessary integration into the other parts of IT that are quite often overlooked. Not only do you need the required level of protection in the form of systems, but it also must be integrated into your maintenance, support, backup, and project functions to make sure the system doesn’t begin degrading when switched on. Cyber Security companies that do not offer the integration into the other business functions are only vendors rather than true Cyber Security companies.
In some cases, Securance is all you need, but in others, it is just the beginning.
360 Smart Networks developed Securance over a three year period to represent the new standard in cyber security. The system was built and based on the NIST (National Institute of Standards and Technology) recommendations but was modified to achieve a level of functionality that a true NIST-based system cannot match.
The basic philosophy around Securance can be summarized as the following:
Protect as best you can but assume you are going to fail; detect as best you can but assume you are going to fail; finally, realize that everything you have done will eventually fail… so, have a spectacular Plan B.
The reality is that when it comes to Cyber Security, what we are seeing today is just the beginning.
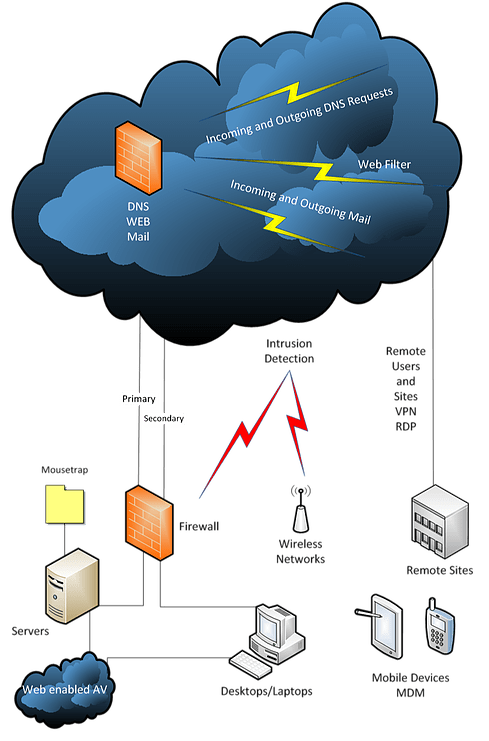
We start with providing a desktop and server anti-virus/anti-malware system integrated into our helpdesk to ensure proactive management. The system will alert us to an issue and open a ticket if it couldn’t remediate the problem. We then reach out manually to intervene.
Next, we install as a standard system DNS and Website filtering. Every request for a destination is filtered against known bad actors and ransomware control servers. This allows us to filter out bad websites that have infected code but also allows a level of ransomware and hacking prevention by being able to identify and block suspicious traffic flow.
As a continuous maintenance function, we strive to keep all our managed systems on patch levels that incorporate the latest updates allowing us to provide ransomware protection against known threats.
360 Smart Networks understands that email is the number one vector for ransomware infection and continues to be the primary entry point for social engineering and phishing operations for hackers. For true hacking and ransomware protection, we use only the premier email overlay systems available.
Scanning incoming and outgoing email is not enough. Securance includes as part of our package, a system that doesn’t just scan and filter email but actually sandboxes them. Every attachment coming into the system is scanned and filtered against known threats but then is opened to observe actual behavior. This allows us to catch exploits before anyone even realizes that a specific vector or file type has been compromised.
Every link in every email is also scanned and followed outside of the system to make sure that it is, in fact, legitimate. No more links that go to infected and risky websites and servers.
The email overlay is not just a ransomware and hacking prevention system but also provides as a standard, features that check boxes for corporate governance and operations. These include a 99-year legal hold and tamper-proof email archive for all incoming and outgoing email independent of the primary email system, a 100% uptime alternative email system in the event of a primary system outage, and Data loss prevention system.
After taking care of endpoint protection, data flows, and email lockdown, 360 Smart Networks goes to work on providing an early detection monitoring system allowing us a level of hacking and breach detection. The specifics of the system is extremely confidential but is built to exploit both automated and human behaviors. Suffice it to say, human nature has its flaws.
Finally, we close the circle with an ongoing Cyber Security training module that incorporates the latest developments in the field. Users are asked to complete training courses designed to make them aware of what the current risks are. After the training, at random intervals, we then “test” their knowledge by sending them false Phishing and virus emails to see if the training actually took. In the event of failure, they are directed to more training and logged as having clicked an unsafe link to be used at a later time, for example, during reviews or operational meetings.
Securance, as a managed cyber security service, returns
the absolute standard in what is needed.
However, as mentioned, in many cases, it constitutes only the beginning. After installation and management of the Securance technology stack and protocols, 360 Smart Networks moves into phase two – raising the walls. We’ve built the basics with Securance but we now apply systems and protocols custom-fitted to your business. During this process, we identify specific federal, state, and industry requirements to make sure you are covered.
Dual-factor authentication, whole disk encryption, and user monitoring are some of the systems we use to make sure our clients stay compliant for HIPAA, FDIC, and SEC regulations in a technical capacity.
As an Atlanta cyber security company, 360 Smart Networks has seen cyber security move from a nuisance to a clear and present danger. Today, as many companies struggle to catch up, we are very proud to be able to offer a complete cyber security system to protect, detect and remediate.
Components:
AV/Malware Scanning, Real-time Protection, DNS Filtering, DNS Scanning, Web Filter, Web Monitoring, Automatic Script Block, Firewall, Mail Scanning, 100% Mail Uptime, 360 Mousetrap, Intrusion Detection, Phishing Testing, Security Training, Traffic Monitoring, Security Audits, Remediation, Reporting, Documentation,
Policies, Mail Archiving, Legal Hold, Leak Protection, e-Discovery
Systems:
Windows Servers, Desktops, Laptops, Tablets, IOS and Android, and Browsers